The Daily Escape:

Wildflowers, Ennis, TX – April 2023 photo by Teresa Gawor
Welcome to the start of taxpayer’s blues weekend. The date for submitting your taxes is April 18 this year, since April 15 falls on a Saturday and Emancipation Day, a holiday observed in Washington, DC, is April 17. Around 88 million Americans still hadn’t filed by April 1, so there’s got to be some burning of the midnight oil this weekend.
Let’s talk about the leak of classified Pentagon documents by Jack Teixeira, a 21 year-old member of the intelligence wing of the Massachusetts Air National Guard. Teixeira was arrested on Thursday for posting US secret documents in a private Discord chat room he hosted. The classified material was shared with some 20-30 room members, including some of whom were foreigners.
The details are depressing. The group had a taste for racist and anti-Semitic memes. The WaPo reports that they seemed to love guns, military gear and God.
What happens next will be a damage assessment by the US Intelligence Community (IC), along with some of the usual suspects staking out political positions about how inept the IC is by allowing another classified leak.
Sadly, Teixeira has already picked up supporters in the GOP, as this tweet by Rep. Marjorie Taylor Greene (R-GA) shows:
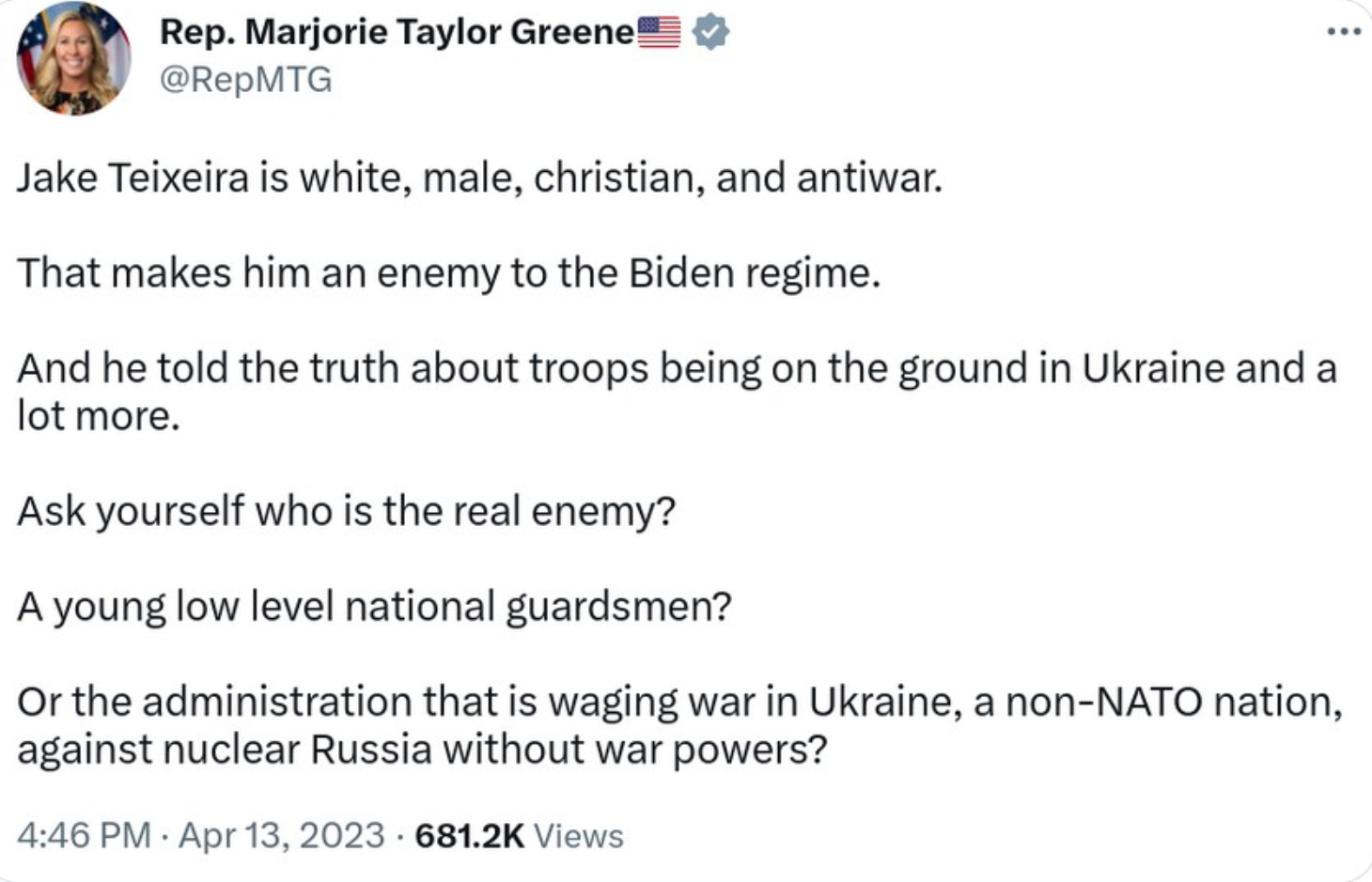
It’s surprising how open and direct the pro-Putin Right is in linking Russia’s policies to those of the authoritarian white Christian secession movement in America. If you read Wrongo’s column yesterday on what’s dividing America, today’s tweet by Greene is a prime example of the difficulty in finding common cause with the extremist wing of the Republican Party.
Perhaps you didn’t see that Fox’s Tucker Carlson said that Teixeira deserves a medal not prison time. Or that he said that Teixeira is today’s Daniel Ellsberg. Others are saying that the racist meme and the god and guns framing aren’t true and are simply what the liberals at the DOJ and the NYT are spoon feeding to us. If you can stomach it, read some of the comments Right Wingers leave after viewing Tucker’s spew.
If this had happened when GW Bush was president, the GOP would be demanding that Teixeira receive a public execution.
But the GOP has moved on, and now there isn’t a substantial difference between Trump and Teixeira. The crimes are the same, and it seems, so are their motives. But Trump isn’t a 21-year old trying to impress his friends in a private forum. After four years as US president, he knows exactly why his behavior was criminal and dangerous.
And whatever sentence Teixeira receives should also apply to Trump, only with less leniency.
A basic question for the US Intelligence Community is how many more disaffected people are out there who have access to our intelligence? How many have a desire to steal it, either to stick it to the man or to simply hoard a few secrets? How many more IC oddballs are out there living in houses filled with terabytes of digital and paper secrets squirreled away?
That’s enough for today, it’s time for our Saturday Soother, where we block out all distractions and try to figure out how many miles our cars were driven for business in 2022.
Here on the fields of Wrong, it’s been in the high 80’s and it’s suddenly apparent that there’s plenty of yard work that needs doing. Wrongo has started trimming and shaping the bushes that seemed to grow wildly last year, even without much rain. Ms. Right helpfully says just chain saw them off to half their size. It will be brutal, but effective!
But before starting the yard work, let’s take a few minutes to center ourselves and try to prepare for the week to come.
Start by finding a seat near an open window. Now, watch and listen to the Vienna Philharmonic play Offenbach’s “Les Contes d’Hoffmann: Barcarolle” live and outdoors in Vienna in 2020. Here the orchestra is conducted by Valery Gergiev. Barcarolle comes from the Italian “barca” or boat. It is a traditional folk song sung by Venetian gondoliers, or a piece of music composed in that style: